Install ldap server
Click here to load reader
-
Upload
mawardi-12 -
Category
Software
-
view
50 -
download
2
Transcript of Install ldap server

Install LDAP server (plus phpLDAPadmin)
LDAP atau Lightweight Directory Access Protocol adalah protokol aplikasi untuk melakukan
query dan perubahan layanan direktori melalui TCP/IP. Sedangkan direktori disini yang dimaksud
adalah sekumpulan obyek yang memiliki atribut yang secara logika maupun hirarki terorganisasi
dengan baik. Sebagai contoh adalah direktori telpon yang berisi nama (orang maupun
perusahaan) dikelompokkan secara alpabetis, dimana setiap nama memiliki alamat, no telpon dan
lain-lain.
Pemanfaatan lain LDAP ini biasanya dipakai untuk melaukan layanan otentifikasi, terkait dengan
permasalahan keamanan seperti jaringan komputer, sistem informasi, dll.
Cara instalasi di CENTOS yaitu :
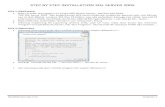
1. Jalankan terminal 2. install openldap
#yum install openldap openldap-clients openldap-servers
3. Konfigurasi ldapserver,
Buat LDAP root user password
#slappasswd
New password: —> misalnya masukkan 123456 sebagai password
Re-enter new password:
{SSHA}+7NhMdrO/CU1ToxihSPH74/NpQNBMh5h
4. Ubah setup slapd.conf, yang BOLD yang saya ubah
#vi /etc/openldap/slapd.conf#
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
# Allow LDAPv2 client connections. This is NOT the default.
allow bind_v2

# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#referral ldap://root.openldap.org
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
# Load dynamic backend modules:
# modulepath /usr/lib/openldap
# moduleload back_bdb.la
# moduleload back_ldap.la
# moduleload back_ldbm.la
# moduleload back_passwd.la
# moduleload back_shell.la
# The next three lines allow use of TLS for encrypting connections using a
# dummy test certificate which you can generate by changing to
# /etc/pki/tls/certs, running “make slapd.pem”, and fixing permissions on
# slapd.pem so that the ldap user or group can read it. Your client software
# may balk at self-signed certificates, however.
# pastikan dahulu letak folder file berikut, gunakan perintah #find / -name ‘ca-
bundle.crt’
TLSCACertificateFile /etc/pki/tls/certs/ca-bundle.crt
TLSCertificateFile /etc/pki/tls/certs/slapd.pem
TLSCertificateKeyFile /etc/pki/tls/certs/slapd.pem
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 63-bit encryption for simple bind
# security ssf=1 update_ssf=112 simple_bind=64
# Sample access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
# Directives needed to implement policy:
# access to dn.base=”” by * read

# access to dn.base=”cn=Subschema” by * read
# access to *
# by self write
# by users read
# by anonymous auth
access to * by * read
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., “access to * by * read”)
#
# rootdn can always read and write EVERYTHING!
########################################################
###############
# ldbm and/or bdb database definitions
########################################################
###############
database bdb
suffix “dc=uii,dc=ac,dc=id”
rootdn “cn=Manager,dc=uii,dc=ac,dc=id”
# Cleartext passwords, especially for the rootdn, should
# be avoided. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
# rootpw 123456
rootpw {SSHA}+7NhMdrO/CU1ToxihSPH74/NpQNBMh5h
# The database directory MUST exist prior to running slapd AND
# should only be accessible by the slapd and slap tools.
# Mode 700 recommended.
directory /var/lib/ldap
loglevel 256
lastmod on
schemacheck on
cachesize 100000
# Indices to maintain for this database
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub

# Replicas of this database
#replogfile /var/lib/ldap/openldap-master-replog
#replica host=ldap-1.example.com:389 starttls=critical
# bindmethod=sasl saslmech=GSSAPI
# authcId=host/[email protected]
5. Copy file konfigurasi database LDAP
# cp /etc/openldap/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
6. Jalankan LDAP server
# service ldap start
7. setup LDAP agar otomatis start saat Centos booting
# chkconfig –level 235 ldap on
8. Inisialisasi LDAP root
# vi ldap_root.ldif
isikan dengan data berikut :
dn: dc=uii,dc=ac,dc=id
dc: uii
description: LDAP Admin
objectClass: dcObject
objectClass: organizationalUnit
ou: rootobject
dn: ou=People, dc=uii,dc=ac,dc=id
ou: People
description: Users of UII
objectClass: organizationalUnit
tambahkan data ke servel ldap, dengan perintah berikut :
# ldapadd -x -D “cn=Manager,dc=uii,dc=ac,dc=id” -W -f ldap_root.ldif
9. install web server untuk manajemen ldap server
# yum install httpd php-mbstring php-ldap
10. Download phpldapadmin dari
website http://phpldapadmin.sourceforge.net/download.php, cari versi yang terakhir

#wget http://internode.dl.sourceforge.net/sourceforge/phpldapadmin/phpldapadmin-
1.1.0.5.zip
11. install phpldapadmin sebagai halaman utama dari webserver di /var/www/html
#unzip phpldapadmin-1.1.0.5.zip -d /var/www/
#cp /var/www/phpldapadmin-1.1.0 /var/www/html -R
12. konfigurasi phpLDAPadmin
#cp /var/www/htm/config.php.example /var/www/html/config/config.php
#vi /var/www/html/config/config.php
lakukan editing bagian server agar terhubung ke server ldap:
/*********************************************/
/* Define your LDAP servers in this section */
/*********************************************/
$i=0;
$ldapservers = new LDAPServers;
/* A convenient name that will appear in the tree viewer and throughout
phpLDAPadmin to identify this LDAP server to users. */
$ldapservers->SetValue($i,’server’,’name’,’UII LDAP Server’);
/* Examples:
‘ldap.example.com’,
‘ldaps://ldap.example.com/’,
‘ldapi://%2fusr%local%2fvar%2frun%2fldapi’
(Unix socket at /usr/local/var/run/ldap) */
$ldapservers->SetValue($i,’server’,’host’,’127.0.0.1′);
/* The port your LDAP server listens on (no quotes). 389 is standard. */
$ldapservers->SetValue($i,’server’,’port’,’389′);
/* Array of base DNs of your LDAP server. Leave this blank to have phpLDAPadmin
auto-detect it for you. */
// $ldapservers->SetValue($i,’server’,’base’,array(”));
/* Four options for auth_type:
1. ‘cookie': you will login via a web form, and a client-side cookie will
store your login dn and password.
2. ‘session': same as cookie but your login dn and password are stored on the
web server in a persistent session variable.
3. ‘http': same as session but your login dn and password are retrieved via

HTTP authentication.
4. ‘config': specify your login dn and password here in this config file. No
login will be required to use phpLDAPadmin for this server.
Choose wisely to protect your authentication information appropriately for
your situation. If you choose ‘cookie’, your cookie contents will be
encrypted using blowfish and the secret your specify above as
session['blowfish']. */
$ldapservers->SetValue($i,’server’,’auth_type’,’cookie’);
/* The DN of the user for phpLDAPadmin to bind with. For anonymous binds or
‘cookie’ or ‘session’ auth_types, LEAVE THE LOGIN_DN AND LOGIN_PASS BLANK. If
you specify a login_attr in conjunction with a cookie or session auth_type,
then you can also specify the login_dn/login_pass here for searching the
directory for users (ie, if your LDAP server does not allow anonymous binds. */
$ldapservers->SetValue($i,’login’,’dn’,’cn=Manager,dc=uii,dc=ac,dc=id’);
# $ldapservers->SetValue($i,’login’,’dn’,’cn=Manager,dc=example,dc=com’);
/* Your LDAP password. If you specified an empty login_dn above, this MUST also
be blank. */
$ldapservers->SetValue($i,’login’,’pass’,”);
# $ldapservers->SetValue($i,’login’,’pass’,’secret’);
/* Use TLS (Transport Layer Security) to connect to the LDAP server. */
$ldapservers->SetValue($i,’server’,’tls’,false);
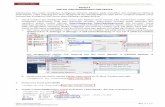
13. Tes dengan browser
Berhasil, alhamdulillah